A: The short answer is, it's at risk. When you install a browser extension, you are opening up your browser—and all the websites you visit—to that extension. Many people believe they are protected by their browser's security, but an extension can bypass those protections to access your personal information.
A: The danger of a malicious extension isn't always obvious. For example, an extension that simply changes the color of a webpage might also be programmed to read the data on that page without your permission. Additionally, many extensions can be updated silently. This means an extension that was safe when you installed it could become malicious after a silent update by the developer.
A: When you install an extension, you grant it certain permissions. These permissions often include the power to "read and change all your data on all websites you visit."
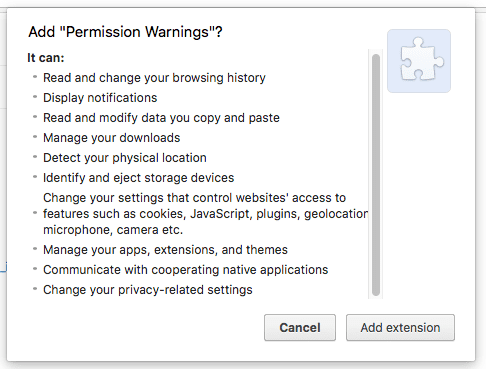
This access gives the extension the power to read everything on a page, including the information you type into forms, your passwords, and credit card numbers. This happens in the background without any visible signs.
A: A malicious extension can do more than just steal passwords. Because it has broad access to the websites you visit, it can:
- Manipulate your actions: An extension can secretly change what happens when you click a button. For example, when you click "Buy Now," the extension could reroute the payment to a fraudulent account without you knowing.
- Change the data you send: An extension can secretly change the information you are sending to a website. For example, on a money transfer site, it could change the bank account number you entered to a different one.
- Inject fake content: An extension can add its own code to a webpage. This could be used to display fake pop-ups, inject ads, or even add a fake login form on a trusted website (like your bank) to steal your username and password.
- Steal your session: An extension can read and steal your session information, which is a small piece of data that keeps you logged in. With this information, the attacker can impersonate you and access your accounts without needing your password.
- Deceive you into thinking the website is acting: An extension can manipulate what you see on a webpage to trick you into believing you're getting a special benefit. For example, it could show you a fake discount code or a cashback offer on an e-commerce site, making you happy with your purchase. In reality, the extension has an agreement with the retailer to get a commission on the sale, and you never receive the promised discount or cashback.
For a visual explanation of how browser extensions can pose a threat, watch this video:
Watch Video: Understanding Browser Extension Threats
Watch Video: Understanding Browser Extension Threats
How an Extension Can Hijack Website you visit (Code Example):
This simplified code demonstrates how a malicious extension could register itself at the window level with the capturing phase enabled. This allows it to intercept events like clicks *before* your website's own JavaScript has a chance to react, giving it the ability to manipulate or even block actions.
// This code simulates a malicious browser extension's content script.
// It would be injected into the page's context.
// Listen for a click event on the entire window during the capturing phase.
// Setting 'true' as the third argument (useCapture) is critical here.
window.addEventListener('click', function(event) {
console.warn('⚠️ Malicious Extension Intercepted Click!');
console.warn('Target element:', event.target);
console.warn('Event type:', event.type);
// Example of data harvesting:
// If the clicked element is a button within a form,
// a real extension could read nearby input field values.
if (event.target.tagName === 'BUTTON' || event.target.closest('form')) {
console.warn('Potential form interaction detected. Collecting data...');
// In a real scenario, the extension would gather data from form fields
// e.g., document.querySelector('#passwordField').value
// and send it to an attacker's server.
}
// Example of manipulation:
// The extension could change the default behavior of the event.
// For instance, preventing navigation or form submission.
// Uncomment the line below to see it prevent other listeners and default actions:
// event.stopImmediatePropagation();
// event.preventDefault(); // Prevents default action (e.g., following a link)
// Example of injecting content (though done via DOM manipulation,
// not event manipulation directly from this handler)
// const injectedDiv = document.createElement('div');
// injectedDiv.textContent = 'Malicious content injected!';
// injectedDiv.style = 'position: fixed; top: 10px; right: 10px; background: red; color: white; padding: 5px; z-index: 9999;';
// document.body.appendChild(injectedDiv);
}, true); // The 'true' here means this listener fires during the CAPTURING phase
Note: In a real browser extension, this JavaScript code would be part of a content script. The `window.addEventListener('click', ..., true)` part is crucial, as `true` makes it a **capturing phase listener**. This means it intercepts the event as it travels *down* to the target element, giving it a head start over most website-registered listeners (which typically use the default bubbling phase). If the `event.stopImmediatePropagation()` line were uncommented in a real extension, it would prevent your website's own click handlers for that element from ever executing.
A: You are in control of your browser. To protect yourself, you should:
- Check Permissions: Always review the permissions an extension requests before you install it. If an extension requests access to "all your data on all websites," it's a big red flag.
- Audit Your Extensions: Regularly review the extensions you have installed and remove any that you no longer use or don't trust.
- Use Official Stores, But Be Cautious: You should only download extensions from official browser stores like the Chrome Web Store or Firefox Add-ons. While these stores provide a level of security, they are not a guarantee of safety.
A: The most important thing to remember is that installing an extension is like giving up control of your privacy and security. By installing an extension, you are trusting a third-party developer with the ability to see and interact with all of the data on the websites you visit. You have no control over what that developer does with your information, or if their extension is silently updated to become malicious in the future. Therefore, you should be very selective about which extensions you choose to install.
A: We have built many internal tools to provide you with safe, secure access without compromising your privacy and security.
The entire suite of zero-installation tools—including Web Conferencing, Note Taking, Task and Reminders, Note Sharing, and Voice Recording — is designed to enhance productivity while upholding the highest standards of privacy and security.
You can confidently use these tools and take advantage of the protection we offer.